How SME Companies Can Prepare for New Data Privacy and Cybersecurity Regulations
 New regulations on data privacy may catch small and medium-sized (SME) companies unaware and under-prepared. Indonesia provides an excellent example of upcoming changes and how SME companies around the world can prepare.
New regulations on data privacy may catch small and medium-sized (SME) companies unaware and under-prepared. Indonesia provides an excellent example of upcoming changes and how SME companies around the world can prepare.
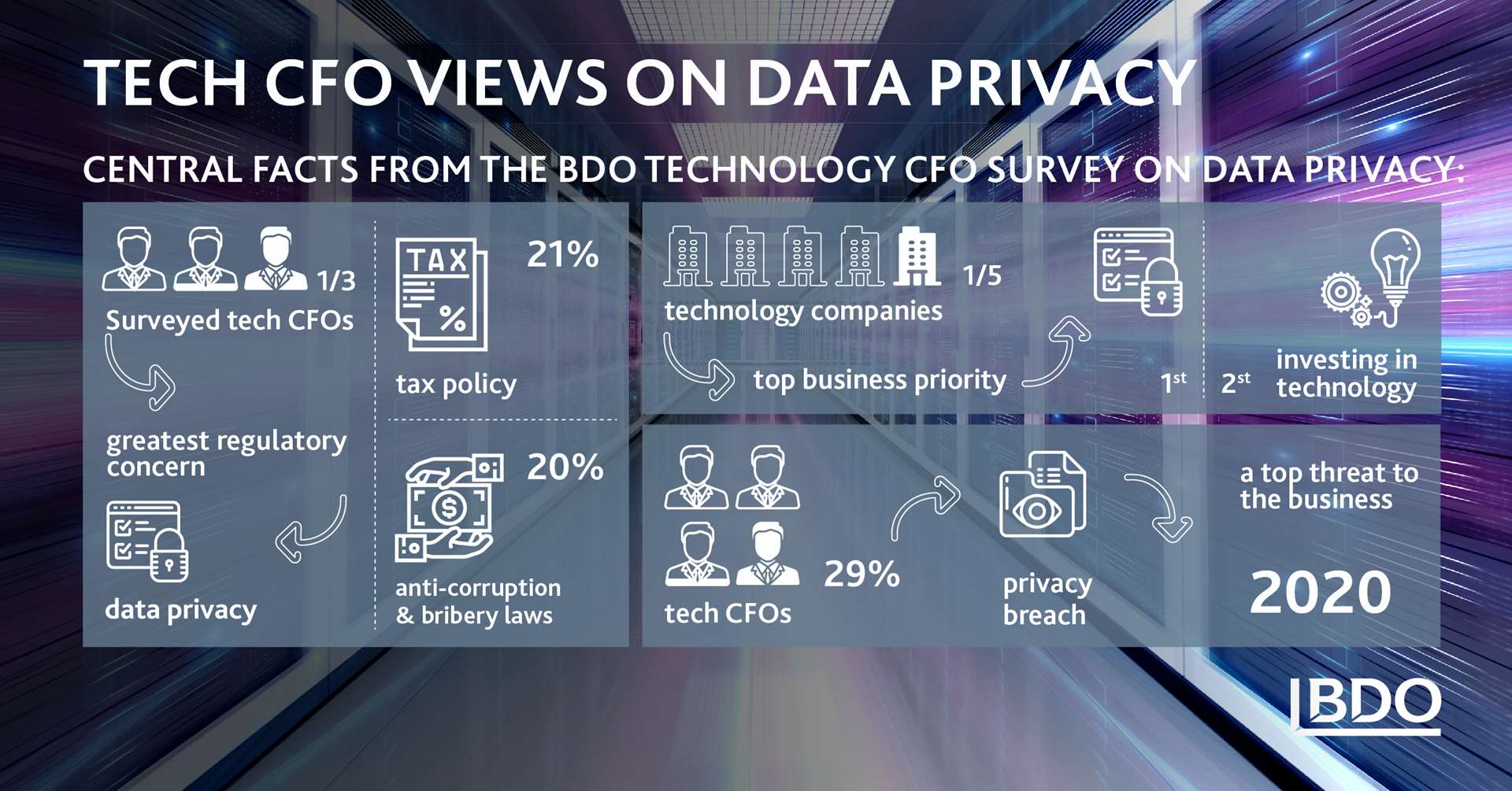
Immediately following an adequate response to COVID-19 business challenges, data privacy and cybersecurity are one of the more significant challenges for companies in 2020. In the recent, pre-COVID, BDO Technology CFO Survey, CFOs point to data privacy as a top regulatory concern and business threat. Our 2018/2019 Cyber Security Survey also highlighted a similar view on general cyber-related risks among management teams.
 Companies and their executives risk monetary fines or, in extreme cases, even prison sentences, not to mention the loss of consumer, market and partner confidence in their brand, if control of data is lost through a cyberattack. Furthermore, compliance requirements of both existing and upcoming data privacy and cybersecurity legislation may catch companies underprepared or unaware, necessitating rapid upgrades that often create knock-on issues.
Companies and their executives risk monetary fines or, in extreme cases, even prison sentences, not to mention the loss of consumer, market and partner confidence in their brand, if control of data is lost through a cyberattack. Furthermore, compliance requirements of both existing and upcoming data privacy and cybersecurity legislation may catch companies underprepared or unaware, necessitating rapid upgrades that often create knock-on issues.
At BDO Indonesia, we consult companies on a variety of challenges within the continually changing landscape of cybersecurity and data privacy. One such challenge will result in 2020 when Indonesia introduces new data privacy legislation. This has led to an uptick in the interest among management teams to upgrade existing setups. However, shortages of in-house expertise and relevant skills often lead to a lack of clarity about how to approach the issue - something that is doubly true for companies in the SME-segment.
Similar situations exist elsewhere as the list of countries introducing privacy laws, which have knock-on effects on cybersecurity matters, continues to grow. In this article, I hope to present some of the issues companies face, using Indonesia as the prime example, as well as make suggestions for ways they can make the most of what might well be a challenging situation.
The International Puzzle
Privacy and cybersecurity have become complex puzzles of overlapping legislation and requirements, depending on where a company is active. In an internet-driven ‘born-global’ era, international operations are the reality for many, including in the start-ups and the SME-segments.
Rules in other territories, including the EU (GDPR) and the US (for example, the California Consumer Privacy Act), already create conundrums for Indonesian companies with operations in these geographies. However, the Indonesian Government’s plans to introduce new laws and regulations could well prove a watershed moment for the nation’s technology, media, and telecommunications industries – and beyond.
As illustrated by the introduction of the GDPR rule set in the EU, SME companies are particularly vulnerable to new regulations, but it can affect all companies, no matter their size.
The Indonesian Situation
A booming digital economy has created many investment opportunities in Indonesia. Companies like Go-Jek are leading the way, but many others, often unknown outside Indonesia, could be heading for greater national and international success.
One of the obstacles standing in their way is a lack of clarity regarding data privacy, which may, among other things, lower consumer trust and thereby hamper growth. As data utilisation becomes a cornerstone of more and more businesses, the need for protection through regulation and enhanced cybersecurity measures becomes ever more important.
A new revision of existing regulation has increased emphasis on improving data privacy protection in electronic systems, transactions and privacy guarantees. Service providers have an obligation to protect data privacy within the following areas of their systems:
- Collection (transparent, purpose limitation, fairness, lawful, data minimisation and required approval from the data owner)
- Processing (analysis, storing, improve and update, publication)
- Removal and erasure
- Notifying the data owner if a leak occurs
The Indonesian Government, together with parliament, is also drafting a personal data protection law, using GDPR as the primary reference. Thus, some fundamental definitions are being used in the proposed law, such as data owner, data subject right, controller and processor.
The owner of personal data will have several rights protected, including:
- The right to know
- The right to access
- The right to rectification
- The right to erasure
- The right to restrict processing
- The right to data portability
- The right to object to data processing
Article 61 to 69 of the proposed law stipulates sanctions, including prison terms (between 2 to 7 years) and fines (between 10 and 70 billion rupiah) for violations.
While some industries, such as telecoms and finance, are quite advanced in their implementation of data protection setups and related cybersecurity measures, many companies in other areas could be in for a very rude awakening.
Potential Roadblocks Ahead
Ensuring compliance with the upcoming rules will likely necessitate both increased understanding of the issues at hand, practical changes, and transformation of company structures.
Current organizational setups often see data privacy and cybersecurity managed by different teams with a Chief Privacy Officer (CPO) in charge of data privacy and a Chief Information Security Officer (CISO) in charge of cybersecurity. Instead, both areas could be managed by a CRO (Chief Risk officer) with oversight from the CEO and board.
CROs can lead to better oversight of privacy strategies, have overall responsibility for navigating the regulatory compliance landscape, and be the authority on risks associated with these two closely related areas.
However, even before such models become effective, decision-makers need to understand data classification and how it governs data privacy and concurrent cybersecurity structures. Without clear classification of what the loss of control over different types of data can lead to, developing efficient protection strategies becomes almost impossible. Since data is the lifeblood of all parts of modern organisations, every business unit must have a baseline understanding of what data flows through it, how to best protect it without leading to inefficiencies, and what new risk mitigating strategies can mean for workflows.
All the above can result in the need for integrating new technological solutions, as well as upgrading the way specific data management tasks are conducted.
Positive Need for Adaptation
The introduction of new compliance rule sets, organisational changes and changing workflows will likely be disruptive. However, the situation also provides companies with new opportunities to initiate proactive changes. Especially if one considers the likely alternative: forced and rushed upgrades close to – or after - the new rules take effect.
For example, the introduction of new data privacy rules is an opportunity to analyse current cybersecurity setups and policies and update them. This will lead to stronger, more efficient setups. Companies may also need to integrate secure by design compliance in software and applications across the company structure. This will, in most cases, lead to stronger, more secure products and solutions, which can make companies more robust and increase trust and confidence among customers and partner organisations.
The exact nature of the required changes and upgrades will vary from company to company and often depend on the business’ maturity level. BDO Indonesia has broad experience with these issues and frequently advises companies from multinational enterprises to SMEs on how to update and improve their data privacy and cybersecurity setups. We help companies ensure a high standard for consumer protection, setting governance standards, understanding the technical realities of any regulation, and avoiding unnecessarily stifling of innovation through restrictive or cumbersome setups.
Our process is based on a detailed analysis of the company’s current situation, its strategic goals, industry standards, and baseline figures for desired improvements. Through this analysis, we can develop – and implement - detailed solutions and strategies that help futureproof our clients.
Carrying out a similar process – either with our assistance or on their own – may be a great starting point for companies that are looking to update their data privacy and cybersecurity setups.